Let us know what type of content you'd like to see more of. Fill out our three question survey.
The Impact of Corruption on Cybersecurity: Rethinking National Strategies Across the Global South
Jul 25, 2024
This is an excerpt from the issue brief published July 1, by the Atlantic Council’s Digital Forensic Research Lab. View the full issue brief here.
“Cyber criminals are coming for the Global South”—Deutsch Welle
The global revolution in information and communications technology has expanded educational and economic opportunities across the Global South even as it brings new threats of inequality and cyber vulnerability. Whether these countries are prepared, they now represent the fastest-growing population of new internet users. Moreover, malicious hackers have recognized this rise in networked users, with Latin America and the Caribbean now leading the globe in the rate of cyberattacks as a share of the networked population, while Africa leads in the rate of cyberattacks per institution.
The process of digital transformation started later in the Global South, which likely limited the vulnerability of these countries to ransomware attacks. This is no longer the case. Vanuatu served as a wake-up call in 2022 when most of the island’s public services shut down after hackers encrypted the government’s data networks. The ransomware gang’s commitment of time and resources to infiltrate Vanuatu’s government networks demonstrates that even the smallest nations in the Global South can no longer assume they will be overlooked by global hacker organizations.
Catching Up
A critical lesson from the first decade of ubiquitous cyberattacks is the importance of patching an enterprise’s network software. Unfortunately, the vulnerabilities that IT professionals must track and patch each year have been growing, especially since the arrival of cryptocurrency in the mid-2010s offered the first practical means for hackers to receive payments after locking up or seizing data.
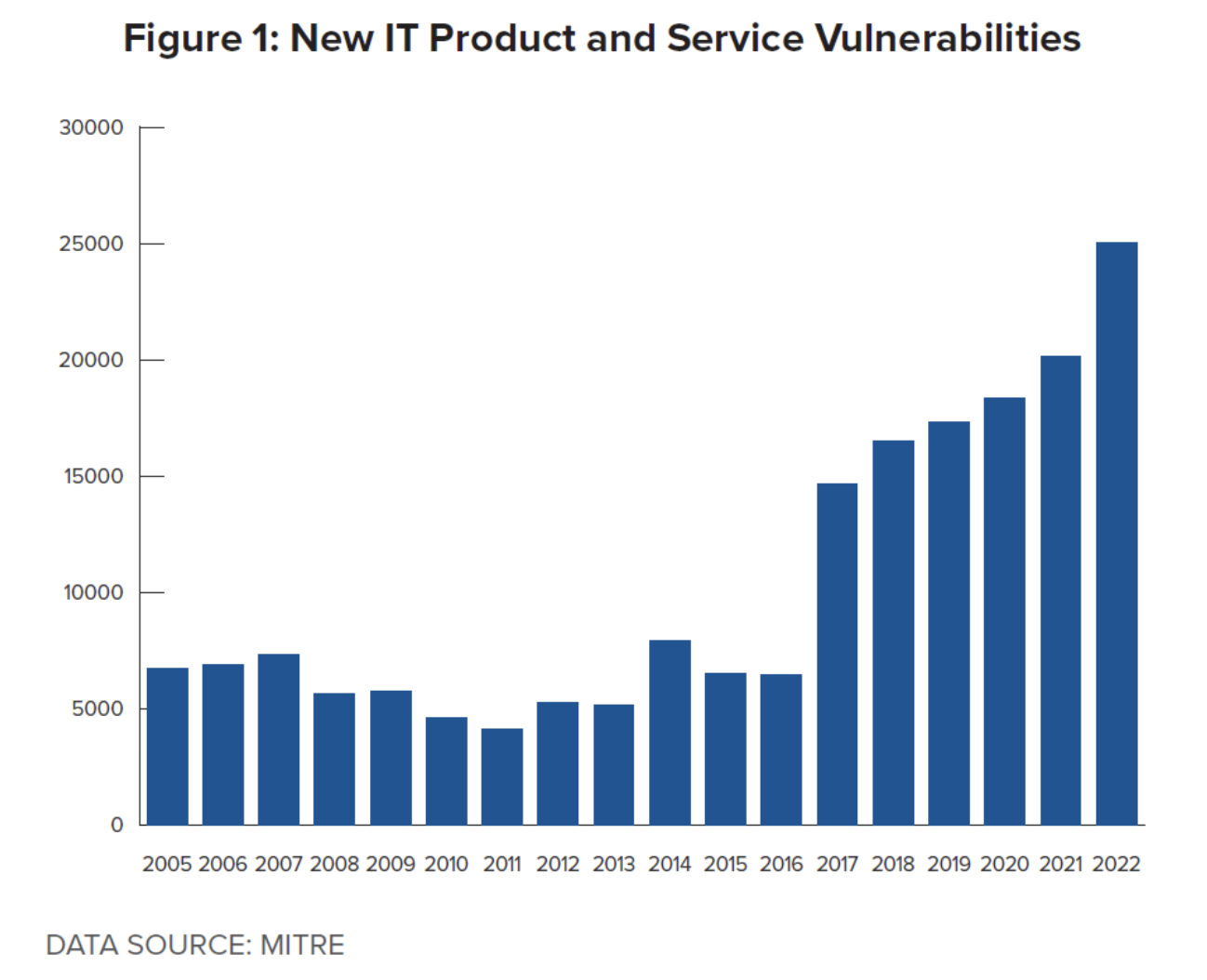
Figure 1 shows MITRE’s recorded annual increase in registered vulnerabilities and exposures, which shows the growth has been rising at an exponential rate since 2018. As ransomware began to grow and criminal organizations sought to continue finding lucrative and vulnerable targets, hackers suddenly turned to institutional networks in countries they might never have heard of before researching potential targets. A growing horde of ransomware organizations appear to be choosing targets based first on vulnerability, which has resulted in more attacks on institutions in the Global South.
Although the need to patch software vulnerabilities has never been higher, corrupt practices in software procurement explain why many organizations do not regularly update their security. Functioning software that was not legitimately acquired rarely provides a connection to the software vendor. The presence of pirated software on a network reduces the likelihood that the network is regularly receiving updates that the software’s producer distributes to patch newly discovered vulnerabilities.
An organization’s cybersecurity can also face vulnerabilities due to obsolete versions of software still running on its network. This can happen for multiple reasons, from vendors going out of business to developers choosing to no longer support a product line. In underfunded institutions across the globe, it is not rare to find the continued use of obsolete software. This vulnerability is further exacerbated by procurement managers prioritizing corrupt rents over issues of trusted vendors or sustainable support for software.
Numerous Barriers to Upgrading Security
Given the epidemic levels of corruption in public and private procurement across the Global South, this study draws from recent cybersecurity experiences in European and Eurasian economies similarly challenged by corruption to argue that a digitally integrated Global South may be more susceptible to cyberattacks than those in the Global North. While the limited scale of the digital economy across most of the Global South continues to keep these countries out of top spots in terms of the total number of attacks, the Global South has suddenly become a disproportionately high malware target. This new reality reflects unique challenges to cybersecurity in the Global South and also suggests that the solutions to this challenge may not be found in the traditional national cybersecurity strategies based on the playbooks of more developed countries.
Robert Peacock is Senior Strategic Technical Advisor for DAI on the USAID Critical Infrastructure Digitalization and Resilience program.
Editor’s Note: Although the term Global South is a preferred term for those nations most challenged in economic growth and good governance, there is no set definition of its membership. This policy brief defines the Global South not by geography or gross national product, but rather by any country that is not one of the top 60 countries in Transparency International’s Global Corruption Perceptions Index (CPI). Therefore, geography is not the defining feature that explains why Uruguay (Latin America’s richest country and 14th ranked by the CPI index) is defined as Global North while Hungary is not.