Let us know what type of content you'd like to see more of. Fill out our three question survey.
Cyber Security Series Part 3: Pirated Software
This post is one of a series of posts on Cyber Security.
Dec 13, 2018
It’s been about two months since I last contributed to the Cyber Security Series, but don’t let the time fool you into thinking we haven’t been engaging extensively on the topic. As many of you might remember, the Center for Digital Acceleration (CDA) published the Digital Inclusion and a Trusted Internet report in October on the topic. For those of you who have not read it, I highly recommend it, particularly if you’re interested in cyber security or data privacy.
The first post in this series focused on the issue of trust and the second post argued that investment in regulations that support the enabling environment, strong institutions, and skills of the population are key to integrating cyber security across a country’s economy. This post focuses on a more micro-level challenge—pirated software—and how addressing it is key to responding to cyber security overall.
The Challenge: Pirated Software is Ubiquitous
Software is used every day by billions of people to conduct tasks for businesses, government, civil society organizations, and academia. It is just another part of people’s routine; arrive to the office, turn on your computer, run a variety of programs, and get to work.
 Each program we use is built by software, a set of protocols that tell the program how to operate. To use software, we pay a fee and run updates to ensure we have access to the latest version. But not everyone pays a fee to gain access. Many around the world pirate software or content to gain access to a myriad of services for free.
Each program we use is built by software, a set of protocols that tell the program how to operate. To use software, we pay a fee and run updates to ensure we have access to the latest version. But not everyone pays a fee to gain access. Many around the world pirate software or content to gain access to a myriad of services for free.
In many low- and middle-income countries, purchasing and installing pirated software to conduct everyday business is common. Reasons for this vary and include high cost, lack of repercussions due to limited regulation, and lack of awareness. Regardless of the explanation, the threats of using pirated software, whether to help run a business or the daily operations of a government, should sound alarms for anyone concerned about cyber security.
Pirated software is often infected with malware. Malware can slow computers or infect computers with instructions to share information with other parties, essentially creating vulnerabilities that can be exploited by a variety of actors. Although most malware is created by criminal organizations with the goal of stealing data or gaining access to money, it can also be used by foreign governments to conduct espionage or damage a country’s critical infrastructure. In other words, installing pirated software can have massive repercussions on an economy, because it can create vulnerabilities across the country’s network, which can then be exploited to conduct a cyber-attack.
For low- and middle-income countries worried about protecting their critical infrastructure—whether it be databases of information or access to networks managing energy supply—taking on the issue of removing pirated software from government systems is essential.
Addressing the Challenge of Malware
If you think of pirated software as only a governance challenge you’re missing the bigger picture. Yes, passing legislation criminalizing the use of pirated software is a step in the right direction, but it does not help address the cost question or the lack of awareness question. Here is where a combination of thinking outside of the box and within some existing development frameworks is helpful.
Cost
Let’s be honest, the cost of software is not cheap, and we sometimes assume it’s expensive. To buy Microsoft Office 365 for one person costs about $70/year. For businesses it can cost more than $100/year to access Microsoft’s services. This is not a negligible cost. If anything, for a small business owner or a civil society organization in a low- or middle-income country, this can be a heavy burden. Similarly, it can be restrictive for governments especially if their budget for IT procurement is already limited, the leadership has other priorities, or there an epidemic of corruption.
Because of cost, installing and using pirated software may seem like an appealing solution in the short term. Yet in the long term, using pirated software can actually exponentially raise costs overall. This figure from a report in 2014 demonstrates just how costly it can be.
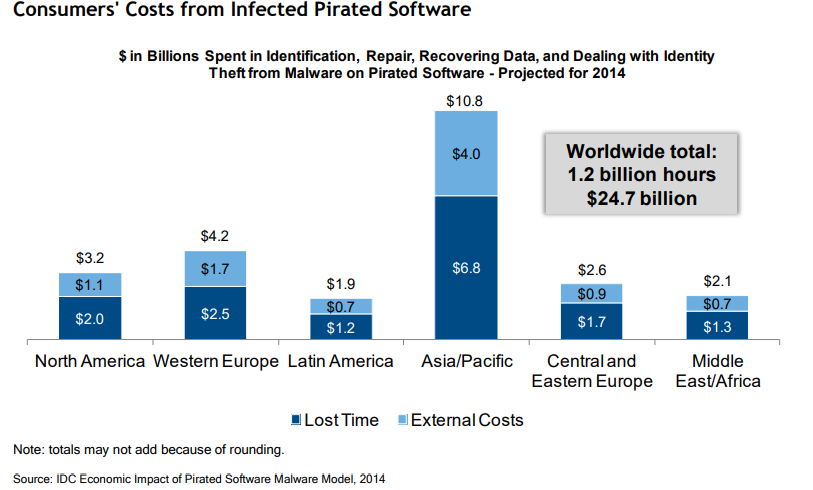
Although the cost for governments was not analyzed in the 2014 report aforementioned, one can only imagine the time and money governments around the world spend (i.e. not cheap!) on fixing vulnerabilities in their systems, assuming they even invest in addressing the problem.
Here is where thinking outside the box can be helpful.
It’s clear governance alone cannot help address the cost problem. Rather, thinking of other useful tools that might supply people, businesses, and governments with reliable software may be more relevant.
Open source software offers an alternative when facing the cost question. In previous blogs we’ve written extensively about the subject and reviewed a range of open source software for data analysis and GIS that are user-friendly. These tools are great for data scientists, but are less useful for the average person who needs a platform to write a report or create a simple budget. Not surprisingly, open source tools exist for more “common” software tools.
Take for example, LibreOffice, a nonprofit that offers a suite of free and open source software mirroring closely the features of Microsoft Office.


Images from the LibreOffice website.
These types of tools give users better choices, and in theory can help prevent the use of pirated software. All that said, using open source tools might not be the best option for government or excuse government from addressing the issue of piracy through legislation. If anything, open source software may just help build a more resilient digital economy, which can be critical when facing cyber security risks.
Lack of Awareness
Lack of awareness can take several forms, but it boils down to limited knowledge. When it comes to software it might mean being unaware that the software you were sold was pirated or not understanding the risks associated with buying and installing pirated programs. Addressing this requires building the skills of people about the risks of pirated software. This is particularly critical for the government, civil society, academia, or the private sector, which might have access to sensitive information.
Building the capacity of professionals around a country will require investments from all four sectors of the economy. This could take the shape of certification programs, like the Kyiv Cyber Academy in Ukraine which was started by ISSP, one of the leading cyber security companies in the country. It could also model off of academic programs like the South African Cyber Security Academic Alliance in South Africa. Or it could reflect the cyber security course created by the UK Government to support businesses in understanding the issue.
Although I personally have not taken these courses and cannot vouch for their effectiveness, the point that local education initiatives, offered in local languages, and with the knowledge of the local context will likely succeed the most in bridging the knowledge gap about the risks associated with using pirated software.
Tying Up Loose Ends: Malware Attacks Impact Us All
Although piracy is a major problem for low- and middle-income countries, it is also a challenge for more advanced economies. The difference is that there tends to be stronger institutions, regulations, and skill levels across high-income countries. That said, the globe is interconnected and the experience of incidents like the WannaCry attack demonstrated the reach, intended and unintended, that malware can have. Given our interconnectedness, addressing the issue will require cross-sectoral and international expertise.